On October 31, 2025, the National Technical Committee 260 on Cybersecurity of SAC (TC260) released a recommended national standard draft titled Data Security Technology – Requirements for Data Security Protection (hereafter referred to as the Draft), which is open for public comments until December 30. The Draft sets forth principles, objectives and a framework for data security protection, specifying general requirements as well as specific requirements for safeguarding key data and core data. It applies to guiding various sectors, regions, departments and data processors in implementing data classification and grading for protection purposes. It may also serve as a reference for competent (regulatory) authorities and thirdparty assessment bodies in supervising, managing and evaluating data security.
In accordance with the GB/T 43697-2024 Data security technology — Rules for data classification and grading, the Draft categorizes data into three levels including general, key, and core data based on factors such as importance, precision, scale, and security risks. Corresponding data security protection measures shall be adopted for each level of data: general data shall be protected as needed while fulfilling legal obligations, key data shall be subject to enhanced protection, and core data shall be managed under strict controls. Meanwhile, the Data Security Protection Framework is formulated as below.
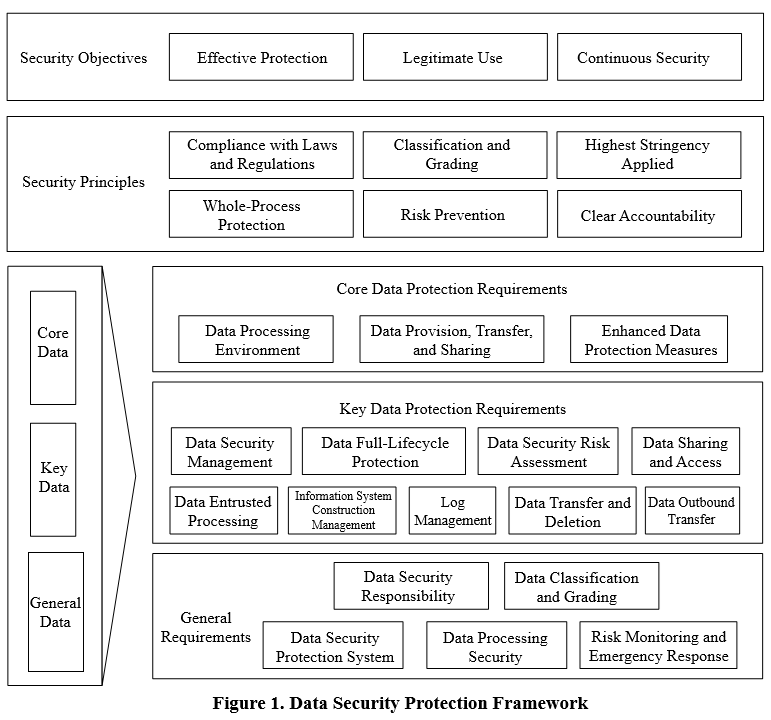
In terms of security protection requirements, general data must fulfill statutory obligations first, then implement need-based protection measures tailored to data security risks by referencing the general requirements, while its free flow is encouraged under the premise of security and compliance. Key data security protection extends beyond general requirements, mandating a dedicated management body, lifecycle technical controls like encryption, compliance with Level 3 or above cybersecurity protection for storage systems, annual risk assessments and reporting, strict oversight of sharing and outsourcing, and operational log retention for one to three years. Moreover, processors of key data must store domestically collected or generated data within China and declare a security assessment for any necessary overseas transfer.
Similarly, the security protection requirements for core data are further strengthened beyond those for key data. Storage and processing systems must comply with Cybersecurity Level 4 protection or critical information infrastructure security requirements. Transfers exceeding 30% of annual cumulative volume to other entities require risk assessment organized by the National Data Security Coordination Office. Priority shall be given to commercial cryptography, secure and trusted products/services, and third-party risk assessments. Key logs related to security incidents must be retained for at least three years, and national security background checks are mandatory for personnel in critical positions.
To summarize, the Draft poses multiple implications for foreign enterprises in China. It introduces stricter data classification, requiring enhanced local storage and outbound assessment for key/core data. Compliance costs will rise due to demands for stronger encryption, logging, and system protection. Data transfer procedures will be more regulated, and personnel in sensitive roles may face national security screenings. Foreign firms must review their data assets and adapt compliance strategies accordingly.
Chinese source of the article: https://www.tc260.org.cn/portal/suggestion-detail/20251031084754