On March 28, 2025, the Cyberspace Administration of China(CAC) released a draft amendment to the Cybersecurity Law (hereinafter referred to as the “amendment”) for public consultation. This is the second proposed revision since China’s the law’s initial enactment in 2017. The first amendment draft was released in 2022.
The amendment aims to coordinate with China’s evolving policy focus on enhancing its national security legal framework and strengthening the institutional capacity in the cybersecurity sector. Its objectives are to build a more unified and coordinated legal liability system, fill existing regulatory gaps, clarify implementation mechanisms, and define clear safety baselines and risk thresholds.
Changes occur in the Chapter Six of the Cybersecurity Law which is about legal liability. The 2025 amendment follows 4 key lines of logic:
I. Adjusting Legal Liability for Network Operation Security
- Revision of Article 59:
Article 59 stipulated penalties for network and the nation’s critical information infrastructure operators with regards to non-compliance with obligations to ensure cyber security. The amendment increases penalties:
- The maximum fine for companies rises from 1 million to 10 million yuan
- The maximum fine for individuals increases from 500,000 to 1 million yuan.
In addition, a new penalty scenario is introduced for causing large-scale data leaks or operational disruption in Critical Information Infrastructure (CII), such as failures in telecommunications network or satellite systems.
Critical Information Infrastructure refers to important network infrastructure and information systems in public telecommunications, information services, energy sources, transportation and other critical industries and domains. The inclusion of CII aims to address new risks and challenges found within China’s cybersecurity system throughout the technological development in the past few years, and reflects China’s intention to adopt a more stringent national security approach to ensure its public interests.
- Addition of Article 61:
New Article 61 makes safety certification and safety testing compulsory. Failure to comply will cause severe penalties. The content of the new provision is provided below:

The new Article 61 also cited Article 23 of the Cybersecurity law which described that network critical equipment and dedicated products for network security must receive certification from a qualified institution in accordance with the mandatory requirements of relevant national standards or pass security testing before they can be sold or provided.
The list of network critical equipment and dedicated products for network security is determined by CAC, in conjunction with relevant departments of the State Council. (View the product catalogue developed by CAC in Chinese language from here). Stakeholders whose products and services are included in this catalogue or are affected by its usage need to familiarize themselves with this Article 61 to avoid significant compliance risks.
- Addition of Article 64:
The new Article 64 in the amendment draft stipulates that:
“Where the acts as prescribed in Paragraph 1 and Paragraph 2 of Article 60 and Article 63 of this Law cause the consequences as prescribed in Paragraph 3 of Article 59 of this Law, the punishment shall be imposed in accordance with the provisions of that paragraph.”
Below is a flowchart that visualizes the mechanism of this clause:
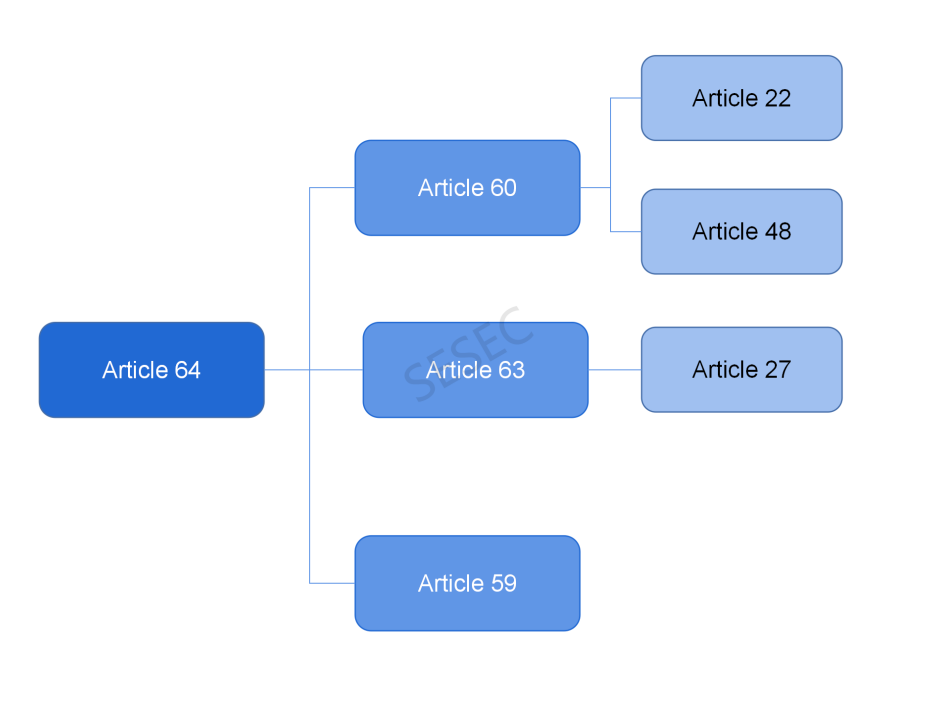
Article 60 addresses the penalties for violation of illegal acts included in Article 22 & 48, while Article 63 address the penalties for violation of illegal acts included in Article 27. The paragraph 3 of Article 59 refers to the newly added legal liabilities concerning cases such as those cause massive data leaks and discontinuity of critical information infrastructure’s operation.
Key related violations under Article 64 include:
- Article 22 – Malicious programs and security flaws found in network products and services of the operators.
- Article 48 – Malicious programs and security flaws found in electronic information sent and application software operated by the relevant service providers.
- Article 27 – Illegal intrusion and stealing of network data of any individual or organization.
However, the difference between existing version and the amendment draft is that the amendment streamlines the penalty mechanism for violations of specific provisions, whereas the existing version establishes penalties separately for each violation.
II. Clarifying Legal Responsibility Regarding Network Information Security
- Merging the original Article 68 & 69 and Increasing Penalties:
The amendment merges the original Article 68 & 69 into a new Article 69 to also streamline the penalty framework but heavier penalties.
Maximum penalties increases from 500,000 to 2 million yuan, with potential escalation to 10 million yuan for severe cases.
Network operators, electronic information transmission service providers, and application software download service providers are identified as parties subject to these penalties.
The focus here is on significantly heightening the cost of non-compliance and misconducts.
III. Specifying Legal Responsibility Regarding the Security of Personal Information and Important Data
The amendment consolidates first paragraph in the original Article 64, the original Article 66 and Article 71 into a new Article 71 in the amendment. This new provision targets cases related to violating laws and regulations of Personal Information.
The new Article also emphasizes CII operators, further reflecting China’s strategic shift towards a more robust CII operator management framework for national security purposes.
IV. Specifying Circumstances Where Administrative Penalties May be Mitigated, Reduced or Waived.
Lastly, the amendment has added a new Article 72, under which administrative penalties may be reduced, mitigated, or waived.

However, this new provision leaves several key points unclear:
- What qualifies as a “minor illegal act”?
- What constitutes “minor harmful consequences”?
- How is the severity assessed, and how are penalty reduction determined?
- What authorities are involved in the evaluations and final decisions?
These ambiguities could create challenges during enforcement. We may expect more details after public consultation in the final draft for official release. Moreover, additional clarifications may emerge through practical application once the amendment is formally adopted and real-world cases arise.
To sum up, what European stakeholders need to take note of in this amendment draft are the potentially hefty compliance cost and the ambiguities surrounding the determination of violation severity and the involvement of CII operators in your business and trade activities. Although foreign stakeholders are unlikely to be designated as CII operators by the Chinese government, the provisions related to CII operators still hold relevance if your products and services are involved. SESEC will continue to monitor developments related to China’s Cybersecurity Law and provide timely updates. We recommend European stakeholders closely follow these changes closely, seeking professional advice and familiarize themselves with the evolving legal framework.
Source:https://www.cac.gov.cn/2025-03/28/c_1744779434867328.htm




