On 25 August 2023, China’s National Information Security Standardization Technical Committee (SAC/TC260) published the draft for comments of the Information security technology – Security requirements for the processing of Key Data (hereinafter referred to as the Security Requirements). This standard plays a crucial role in China’s data grading management system which classifies data into three levels: core data, key data, and generic data. Each level has specific protection requirements and processing measures. The Security Requirements are specifically designed for the handling of key data. The draft is open for public comments until 24 October 2023.
The Security Requirements consist of six main parts: application scope, reference documents, terminology and definition, device security, security of data processing activities, and security of operations and management. It applies not only to entities processing key data but also serves as a reference for supervising authorities, evaluation bodies, and other stakeholders involved in the oversight and evaluation of key data processing activities.
Foreign stakeholders, particularly those engaged in cross-border data transfers, should pay attention to Article 5.4.6 of the Security Requirements. This section outlines the obligations for transferring key data to overseas entities. The requirements include
- Reporting to the Cyberspace Administration of China, and pass the data cross-border security assessment;
- Implementing technical and management measures to carry out cross-border data transfer, commensurate with the established purpose, scope, method, data type scale, etc. of the transfer. Transfer activities will not be allowed if they are inconsistent with the report submitted to the Cyberspace Administration of China for security assessment;
- Receiving and handling user complaints related to cross-border data transfer;
- Keeping the relevant cross-border data transfer log for more than three years;
- Presenting information in plain text and readable form to the competent department or law enforcement department where they are verifying the type and scope of key data to be transferred overseas;
- Ceasingtransfer activities and taking effective measures to protect the security of the data transferred overseas, when the competent authorities do not authorize the transfer;
- Refraining from providing key data stored in China to foreign judicial or law enforcement agencies without the prior approval of the competent authorities of China.
When handling data collected from China, it is crucial for foreign stakeholders to evaluate whether it falls under the category of key data. The Cyber Security Standards Practice Guide – Guidelines on Classification and Classification of Network Data (hereinafter referred to as the Guide), issued by SAC/TC260, provides guidelines for classifying and categorizing network data. It is important to determine the data’s classification by referring to the key data catalogs released by public authorities at the national or industrial level. In cases where catalogs are unavailable, data processors should refer to the key data grading rules and standards that are currently being developed. They should also assess the potential impact of cross-border data transfer on different entities, as outlined in Form 1 from the Guide.
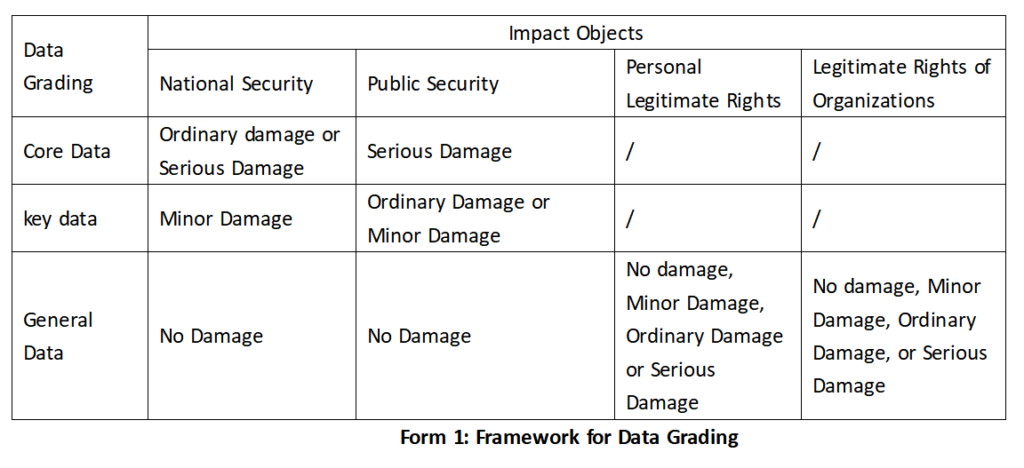
The impact objects are divided into four categories: national security, public interest, personal legitimate rights, and legitimate rights of organizations. Additionally, the level of impact is categorized as serious damage, ordinary damage, minor damage, or no damage. If the data, when tampered with, destroyed, leaked, or illegally obtained or used, has the potential to cause minor damage to national security or ordinary to minor damage to public security, it will be considered key data.